Simplify, Automate and Assess
Your Security Risks
Precision Audit and Confident Compliance help to build strong security posture.
Continuous Assessment to be confident on your security posture
Arix Security Auditor is the proactive auditing solution that empowers your team with an intelligent, automated solutions that cuts through complexity to conduct internal audits at unprecedented speed, accurate and ensuring rapid compliance to strengthen your security posture .
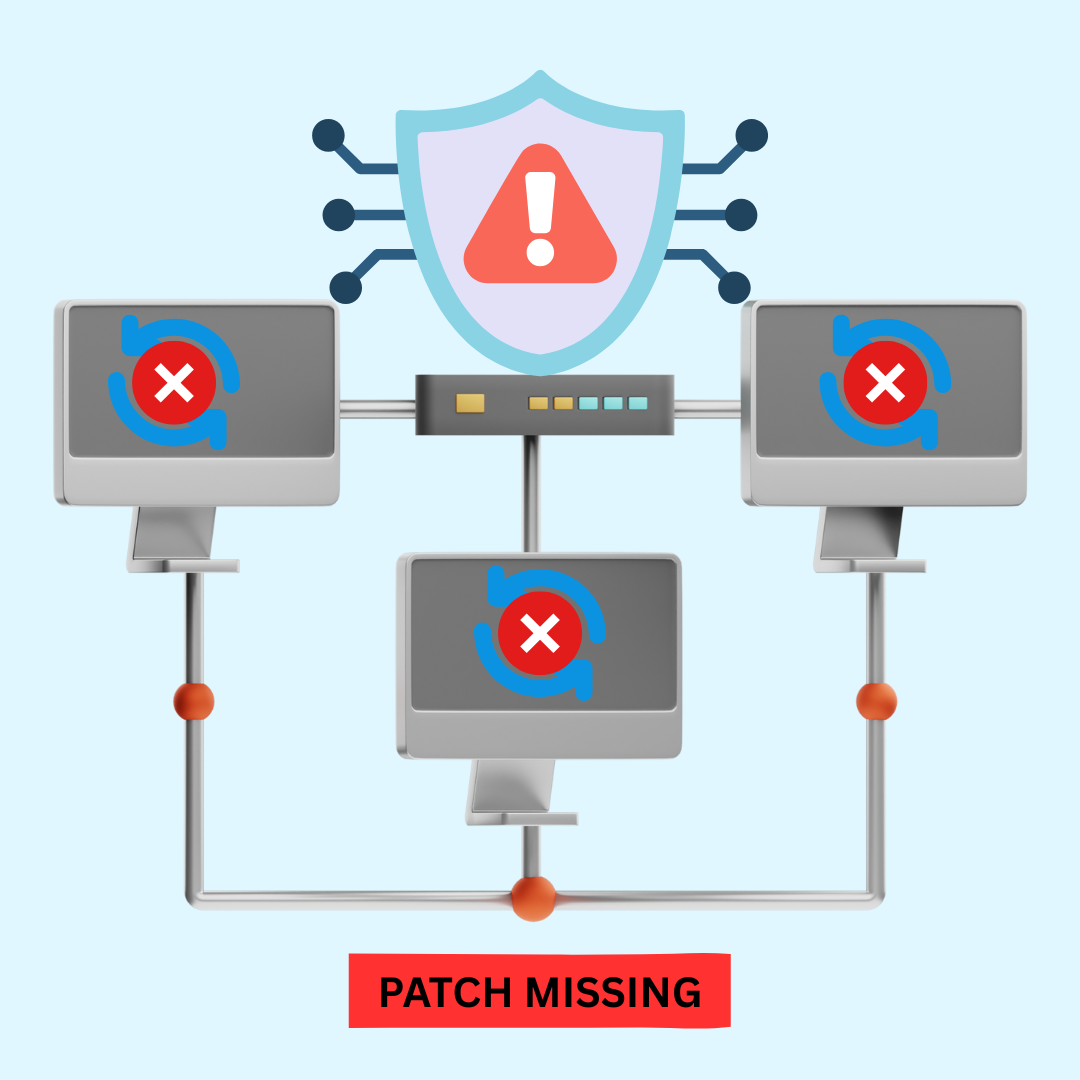
Unpatched Endpoints: Your Greatest Cyber Threat
Discovering the security patch status of every endpoint is a foundational pillar of proactive cybersecurity. In a world of distributed workforces and interconnected devices, each unpatched endpoint represents a potential entry point for ransomware, malware, and other sophisticated threats. Arix Security Auditor gives a platform in which constant visibility allows security teams to identify vulnerabilities early and act on to reduce the attack surfaces from your digital environment.
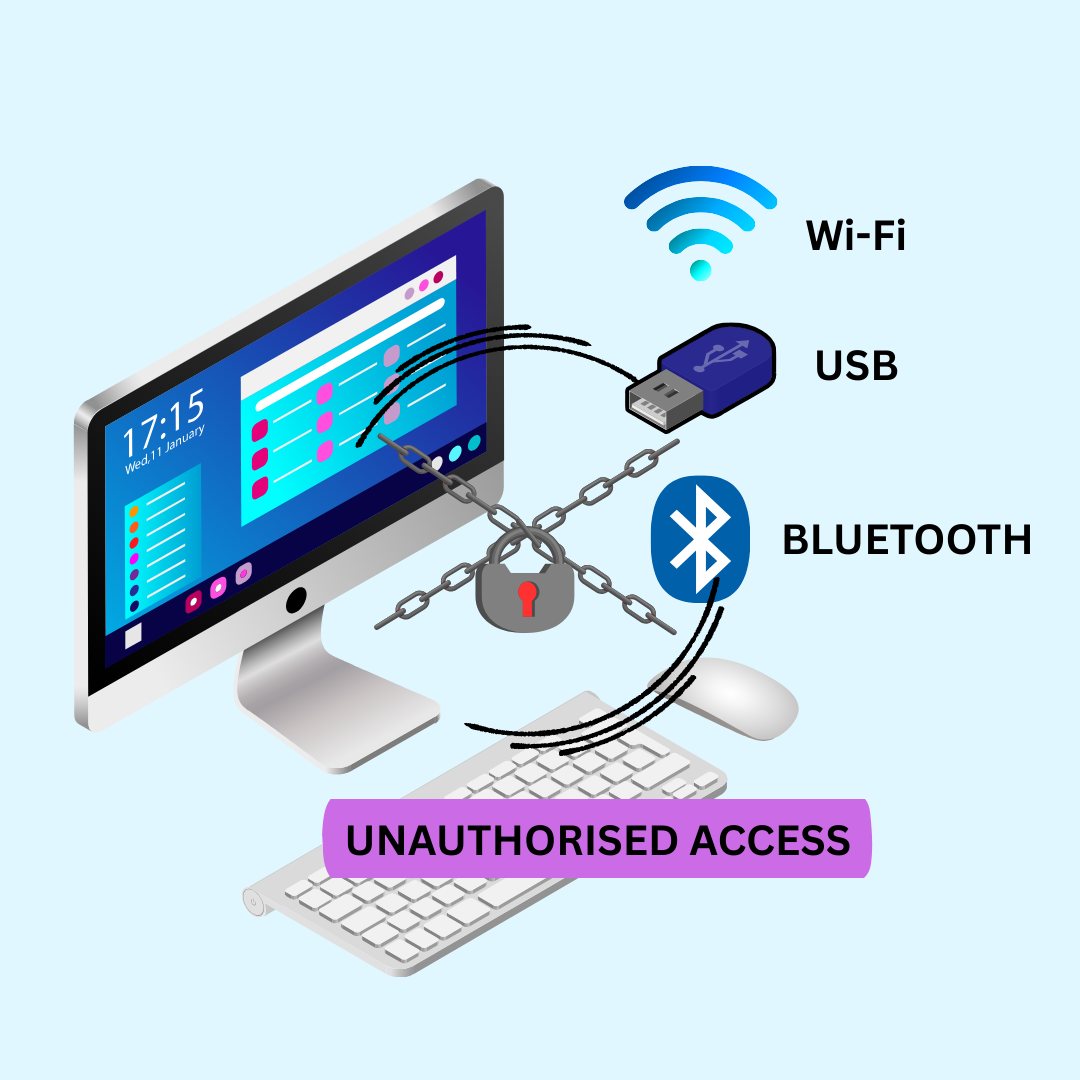
Seal Your Digital Perimeter: Port Monitoring Prevents Data Breaches
Gain total command over your network's physical entry points where data can be transferred. Active monitoring of data ports like Network/WiFi, USB, Bluetooth and other ports, gives you the power to detect and stop unauthorized access for transferring data to external environment. The constant vigilance through Arix Auditor ensures no data can exfiltrate your organization undetected. By preventing malicious or accidental data transfers, you close a critical security gap and protect your most valuable assets from devastating data breaches. Proactive port security is the ultimate line of defense.
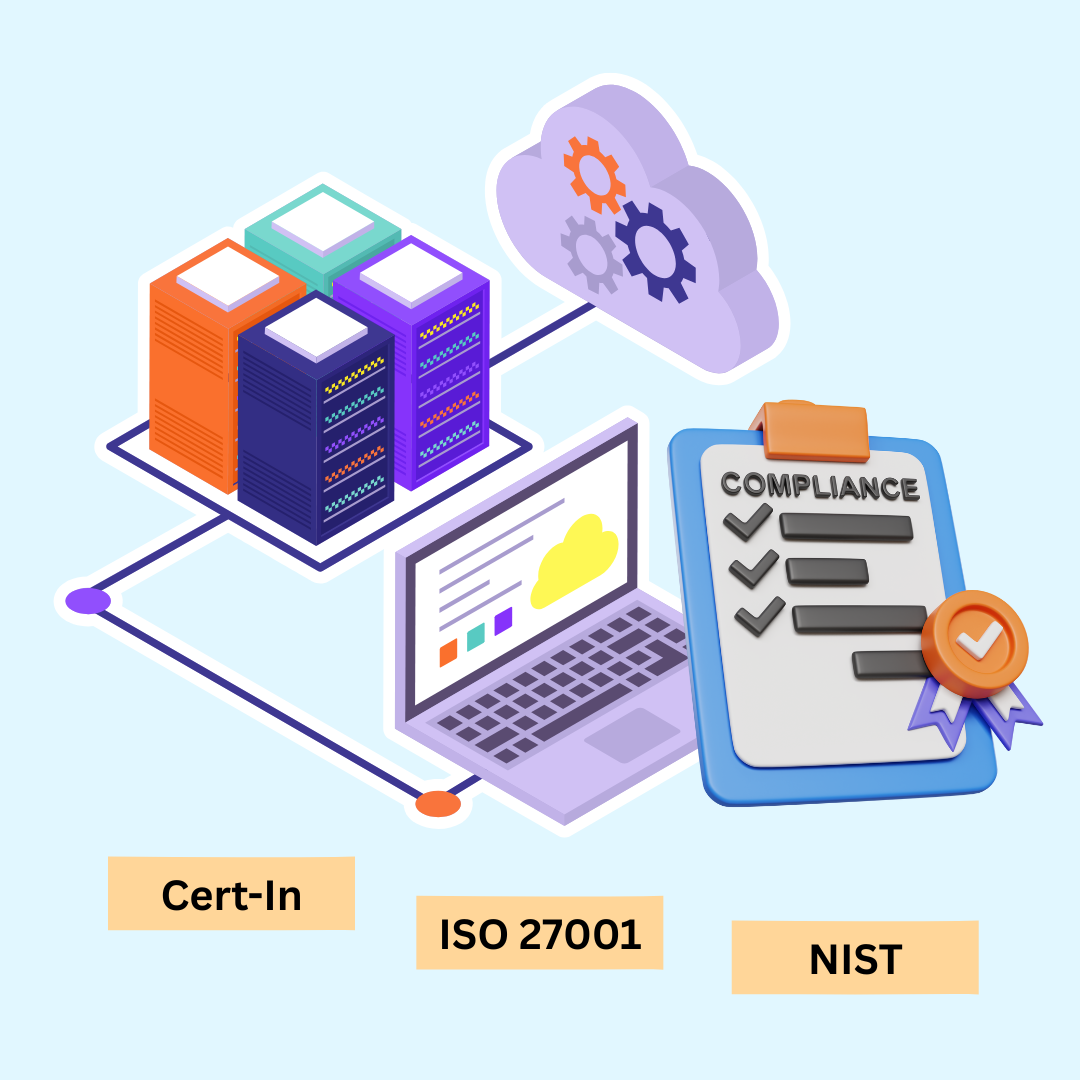
Compliance Audits: Strengthening Security, Ensuring Objectives
Aligning your endpoint audits with defined security policies is crucial for robust governance and risk mitigation. This process moves beyond simple checklist compliance, strategically verifying that controls are in place to actively protect your most critical assets. Arix Security Auditor systematically evaluates referencing security standards and frameworks to identify proactively before it could threaten your entire organization. This not only safeguards against potential legal penalties and financial loss, but also builds invaluable stakeholder trust and strengthens your overall security posture.

Centralized Control: Remote Security Policy Deployment for a Resilient Workforce
Remotely pushing security policies is the critical mechanism for maintaining a consistent and up-to-date security posture across all endpoints, regardless of location. It eliminates manual device-by-device configuration, ensuring all employees adhere to the same rigorous standards. Arix Security Auditor’s centralized security administration control ensures rapid response to new threats, automates critical security measures like patching and access controls, and fortifies your entire network without disrupting remote and hybrid work models.

Scenario 1
Lots of software applications used in our business environment. We are facing difficulties in identifying risky applications installed in endpoints, when a security patch of that risky application is released for a critical vulnerability.

Scenario 2
USB ports are open in our endpoints and we have no control to monitor, who are using USB ports at what times and for what purposes. We want a centralised control mechanism to enable it as per requirement.

Scenario 3
Our company is audited by external auditors in every year. My internal audit team is always busy in identifying non-compliance assets, but still some security policies are missed in endpoints.
FAQ
- Is Arix Security Auditor compatible to linux OS endpoints?
No, Presently endpoint agents are compatible with supported versions of Microsoft Windows.
- What is the pricing model of this platform?
Arix Auditor is available for both subscriptions based (off-premise) and license-based (on-line) pricing model.
- In which environment Arix Auditor can be deployed?
It can be deployed on both on-premise (in your private environment) and off-premise (in cloud based).
- What types of Security Compliance Audit can be carried out through it?
Cert-In, ISO 27001 Information Security Audits can be carried out through it.